Security risks of cloud computing

Moving to the cloud is a significant change, that disrupts many existing processes and habits within an organization. It is also a shift from a legal and security standpoint. Instead of being hosted on-premises, the organization’s data (or at least a part of it) is transferred to a public cloud.
This naturally raises questions about the security of cloud computing. Organizations can legitimately ask themselves: should I entrust my data to an external provider? What are the risks of moving my infrastructure to a public cloud? Isn’t it more secure to keep everything internally?
In this article, we take a look at the security considerations related to cloud computing. We first discuss the level of security that can be expected in the cloud, in comparison with on-premises. Then, we explore the ways organizations can secure their journey to the cloud, by making the right decisions at every stage of their migration.
How secure is cloud computing?
IT security is the primary priority when deploying an application portfolio, and this is true for cloud computing as well as for on-premises environments. This was well explained by Todd Christ, Director of Accelerated Cloud Solutions at Intel, in his interview with us regarding change management in the context of cloud.
Security means building an IT architecture that will stay protected from malicious attacks, and minimize the risk of data breach. For a lot of organizations, another security imperative is to comply with the regulatory requirements of their industry.
In this context, decentralizing an infrastructure and relying on an external provider is a strategic choice for organizations. They need to make sure that, once in the cloud, they will still be able to reproduce the security framework they need to protect their business, and report effectively to regulatory authorities about their practices.
While decentralization of IT and data is a big change, moving to the cloud can actually offer a higher security level than an on-prem environment. There are a few reasons why, and we discuss the two most important ones in the following.

The security expertise of cloud providers
Cloud vendors like Google, AWS and Azure build their entire reputation on their ability to offer flexible, efficient, but also highly secure IT services. Because of that, they are heavily investing in the most advanced technologies and best practices to create a completely secure IT environment. This is a critical expertise nowadays, as fraudsters and cyberattackers are also constantly innovating, and new attack schemes regularly appear.
Organizations do not necessarily have the time, resources and budget to fine-tune their IT security and adapt to ever-evolving threats. Moving to the cloud can then be a way to rely on cloud vendors and their state-of-the-art security frameworks for IT security.
Better disaster recovery
Outage is one of the main risks for an organization’s IT. According to a study conducted by the Uptime Institute in 2022, 60% of the surveyed organizations say they experienced an outage in the past three years. For 34% of these organizations, the outage had a severe or significant impact on their operations.
The survey also found that cloud services are increasingly trusted for mission-critical workloads. Cloud computing can be advantageous when it comes to disaster recovery. Organizations can replicate their data in a secondary data center, in different locations. This way, if one location is affected (for example: after a natural disaster), the data can be retrieved thanks to the backups that were implemented. Setting backup data centers is also more flexible with the cloud, as companies don’t always have the budget and resources to run their own data centers in multiple locations.
Migrate to the cloud in a secure way
As we discussed, cloud computing offers a very high level of security for an IT estate. However, organizations need to carefully plan their migration in order to reproduce their security and compliance standards in their future cloud architecture. In this last section, we discuss a few aspects to consider when managing security aspects during a cloud transformation.

Assessing the existing application portfolio from a risk perspective
The first step of a cloud transformation is to collect information about the current applications of the IT portfolio. This is the occasion to identify the potential risks of migrating an application to the cloud.
The applications that need a closer look are for instance:
- Mission-critical applications, that can affect the continuity of business operations if they stop working.
- Applications that process sensitive or personal information, and where confidentiality is critical.
Assessing applications is a critical part of cloud transformation. This goes beyond risk analysis, and also spans the benefits of moving an application to the cloud. Defining the cloud readiness of an application from a technical standpoint is also important.
For more information about the assessment phase of a cloud transformation, have a look at our dedicated poster.
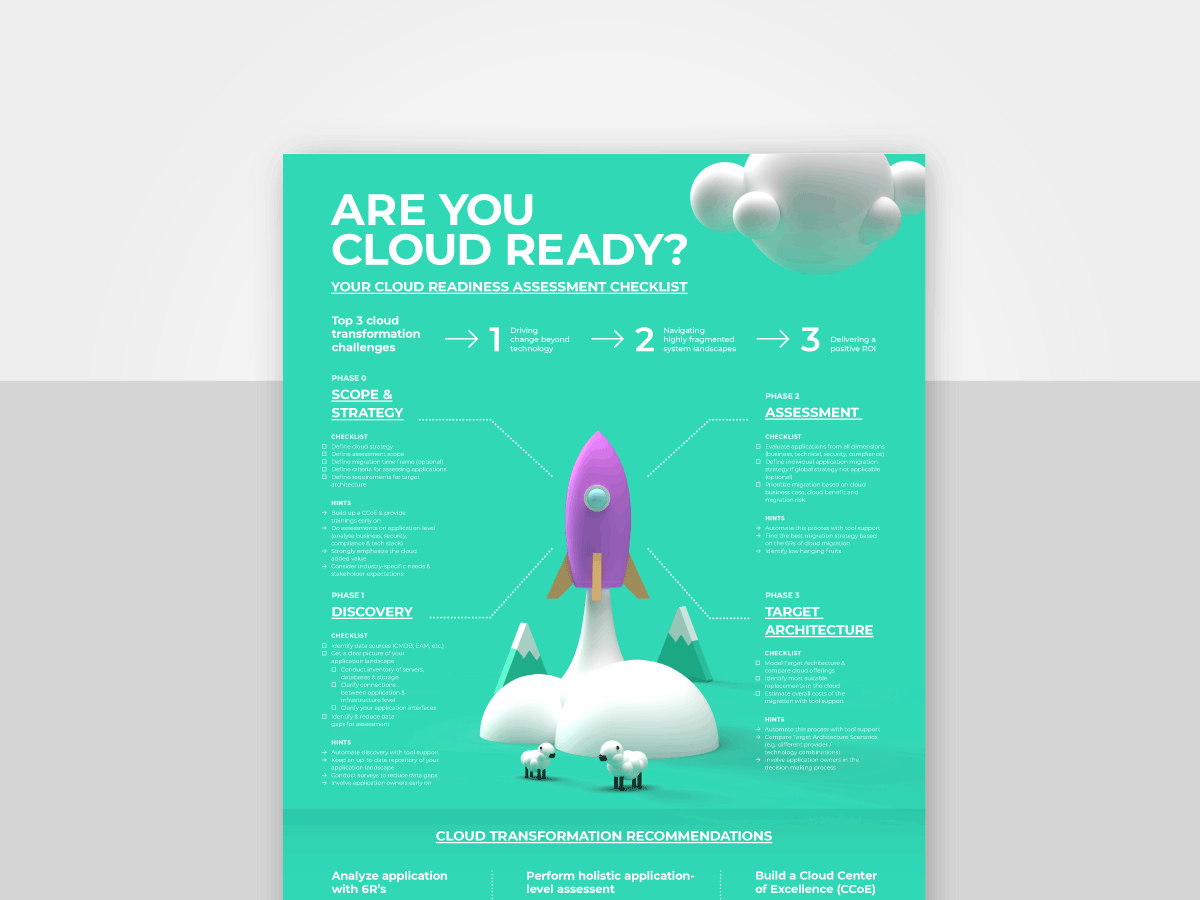
Poster: Cloud Assessment Checklist
Understanding the vendor’s data management process
While outsourcing workloads to a cloud provider can enable more flexibility, scalability, and sometimes cost savings, outsourcing data and workloads might be a challenge from a compliance standpoint. It becomes more difficult to report internally (or to regulatory institutions) when data is stored by a third-party vendor.
When choosing a cloud provider, organizations should clarify the following aspects:
- How data will be stored
- How data will be encrypted
- Who (on the vendor’s side) will be able to access the data
The organization should also check that the cloud services are compliant with the specific certifications of their industry.
Key takeaways
When talking about the security risks of cloud computing, the question is not completely about the security of cloud itself. As for every solution, cloud is subject to threats and malicious attacks. However, major providers are typically implementing state-of-the-art policies and practices for IT security, as it is a significant part of their investments and know-how.
For an organization, the real risk is to migrate their workloads without properly assessing their current IT estate from a security and compliance perspective. When starting a cloud transformation, it is important to perform a risk assessment for every application, and to clarify the cloud vendor’s policies regarding data protection, management and confidentiality.
Assess the migration risk of your applications faster with the Txture platform
Txture is a software platform to plan every step of your cloud transformation, from the initial analysis of your current IT landscape to the definition of a migration roadmap. Txture helps you streamline the process of assessing each application of your portfolio and define their cloud readiness.
Txture also assesses the risks and benefits of migrating each application to the cloud. This helps you identify applications with high cloud business value (e.g., increased performance, increased agility, etc.) for better prioritization of your cloud migration roadmap. It also helps you keep track of applications that process personal or sensitive data, and minimize risk with automated alerts of potential data breaches, or availability issues.
Want to learn more about how we can help you speed up your cloud transformation? Reach out to us, we’ll be happy to answer any questions.
Related posts
11.5.2023Modernization StrategyModernizing legacy IT applications30.3.2023
Cloud Migration Cloud Migration Overview | The 4 Phases & Best Practices6.12.2022
Cloud Target ArchitectureCloud Transformation: how to define the right cloud solution architecture16.11.2022
Cloud AssessmentReady, set, cloud: What is a cloud readiness assessment?2.11.2022
Cloud KnowledgeFaces of Cloud Transformation
